The digital era has ushered in a new wave of innovation and interconnectivity, but along with convenience comes exposure to complex cyber threats. Applications have become the lifeline of modern operations— driving communication, managing services, and delivering user experiences. Whether accessed through smartphones or desktops, they interact with sensitive data that, if mishandled or compromised, can trigger serious consequences. This landscape demands a proactive and continuous approach to securing applications. The concept of “best practice for application security” isn’t a static rulebook, but an evolving framework that must grow alongside threats. The goal is not just to protect data; it’s to preserve trust, reliability, and functionality in an increasingly hostile digital environment. In this blog, we will uncover everything in and around mobile application security and share the best practices to combat the ongoing cyber threats.
What is Mobile Application Security?
Mobile application security refers to the measures and methodologies used to safeguard apps developed for portable devices from cyber threats. This domain covers everything from securing code and encrypting data to assessing how apps interact with external networks and other apps. With billions of mobile users across the globe and countless apps available for download, every vulnerability becomes a potential gateway for intrusion. Mobile applications are unique because they operate in fragmented environments, rely heavily on user permissions, and often run on less secure networks. Ensuring their safety involves far more than testing them before launch; it demands constant monitoring, validation, and updates to combat new vulnerabilities.
The Alarming Rise of Threats Targeting Mobile Applications
The 2025 Global Mobile Threat Report by Zimperium shows how serious mobile security risks have become. With more than 7.2 billion smartphones worldwide and 66% of employees using their personal phones for work, the chances of cyberattacks are higher than ever. Around 23.5% of enterprise devices have sideloaded apps, and 25.2% run outdated systems that can’t be updated, making them easier to target. Mishing, mobile-based phishing— now makes up 54% of iOS threats, with smishing up 22% and vishing up 28% from last year. Also, 23% of enterprise apps connect to high-risk countries, and 18.1% of mobile devices already have malware. Spyware is the most common type, found in 36.9% of malware cases, and banker trojans have gone up by 50% since 2023. These numbers show why it’s important to regularly check apps, verify device security, and stay ahead of new threats.
The Growing Need For Mobile App Security
The surge in mobile device usage has made mobile applications a primary target for cybercriminals. Unlike desktop systems that often benefit from centralized IT oversight, mobile devices frequently operate outside of controlled environments. This increases their susceptibility to phishing, data leakage, and unauthorized access. Moreover, personal and business use often overlap on mobile platforms, introducing risks that could affect entire organizations. Applications often request access to personal information, such as location, contact lists, cameras, or payment details. Without strong security controls, this data can be intercepted or misused. As more services move to mobile-first formats, securing these platforms becomes an absolute necessity for continuity, compliance, and credibility.
Mobile Application Security Checklist
A well-structured security checklist is essential to ensure mobile applications remain resilient against evolving threats and safeguard user data at every stage.
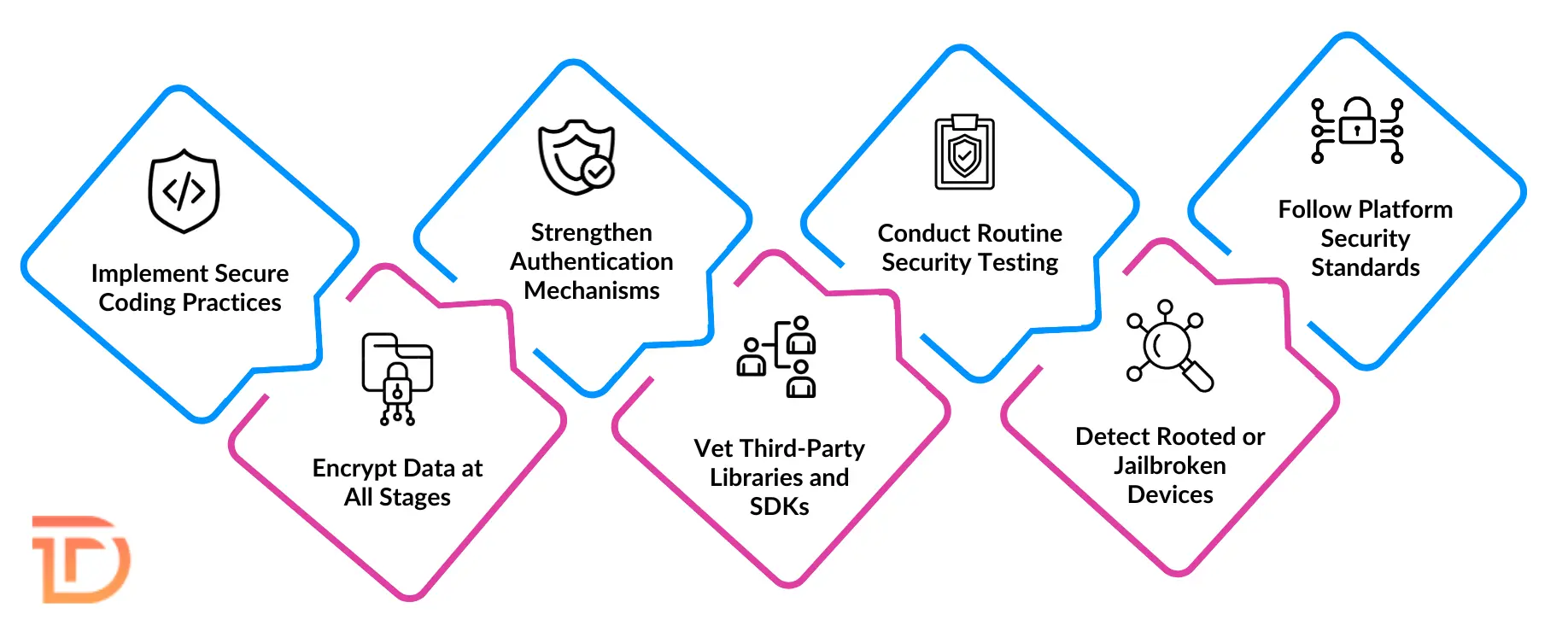
Implement Secure Coding Practices
Use secure coding techniques to prevent common vulnerabilities. Obfuscate the code, validate user inputs, and limit permission requests. These measures reduce the risk of exploitation and make it harder for attackers to reverse-engineer or manipulate your app.
Encrypt Data at All Stages
Protect sensitive information through strong encryption for both data at rest and data in transit. Employ reliable cryptographic algorithms to ensure that intercepted or stolen data remains unreadable and unusable by unauthorized parties throughout its lifecycle.
Strengthen Authentication Mechanisms
Use multifactor authentication to verify user identity. Incorporate session timeouts and biometric options where possible. These safeguards prevent unauthorized access and limit the risk of compromised accounts due to weak or reused passwords.
Vet Third-Party Libraries and SDKs
Assess the origin and behavior of third-party code components. Only integrate libraries from reputable sources and check for recent updates or vulnerabilities. Unverified code can introduce serious security flaws into an otherwise protected application.
Conduct Routine Security Testing
Regularly perform static and dynamic testing to identify security weaknesses. These tests simulate real-world attacks and reveal code or runtime issues early, allowing developers to fix vulnerabilities before users are affected.
Detect Rooted or Jailbroken Devices
Monitor device integrity during runtime. Restrict or disable application functions when a device is detected as rooted or jailbroken, as these conditions often bypass critical operating system protections and increase exposure to malicious interference.
Follow Platform Security Standards
Align with official platform security guidelines and best practices. Ensure compliance with OS-specific rules and regularly update your app to patch vulnerabilities. Keeping pace with evolving threats helps maintain user trust and data safety.
How Do You Maintain Web Application Security?
Web applications demand a distinct yet equally rigorous security approach. Unlike mobile apps that rely on app stores and device capabilities, web apps face threats across browsers, servers, and public-facing interfaces. One of the most fundamental practices is input validation— ensuring that no malicious code or query can be injected through user forms. Secure session handling is equally vital; using encrypted cookies, HTTPS protocols, and controlled login sessions helps reduce the risk of hijacking. Firewalls and intrusion detection systems provide external layers of protection, while regular patching keeps the application shielded from known exploits. Monitoring logs for unusual behavior offers insights into ongoing threats and may uncover attempts before they succeed. Access control, proper user role definition, and database security are other pillars that hold the structure intact. Maintaining security here requires a mix of solid development choices and ongoing vigilance.
Advance Level Practice for Application Security
As threats grow more advanced, so too must the defenses. Basic practices are no longer sufficient on their own. Advanced level practice for application security begins with integrating security into every phase of the development lifecycle. This means adopting a “shift-left” approach where security is not an afterthought, but a foundational element from the design stage. Threat modeling enables teams to anticipate attack vectors before coding even begins. Runtime protection adds another dimension, allowing apps to respond to malicious behavior in real-time rather than just during scans. Security automation speeds up processes without compromising safety, tools can now test thousands of scenarios and review code continuously. For high-risk applications, implementing hardware-backed security keys or biometric validation strengthens access control. Secure containers and microservices architecture allow applications to isolate functions and minimize the impact of a breach. Regular penetration testing by ethical hackers simulates real attacks, identifying weaknesses that automated tools might miss. These advanced measures ensure that applications are not only hardened from outside threats but also resilient against internal oversights.
Understanding Cross-Platform Risks
Applications today are often developed for multiple platforms simultaneously. A single oversight in shared code can open vulnerabilities across all environments. That’s why cross-platform development must include a consistent security strategy that works uniformly yet adapts to platform-specific nuances. Misconfigurations in shared libraries, improper session handling, or inconsistent authentication standards between platforms can introduce blind spots. The challenge lies in maintaining consistency without losing precision. Each platform has its own policies, permissions, and limitations; the security strategy must cater to these specifics while maintaining uniform resilience. This means that every security feature, from encryption to access control, must be revalidated across each platform before launch.
Protecting Application Data Lifecycle
Data doesn’t remain static; it moves, changes, and interacts with others. From the moment data is created, it enters a lifecycle that spans storage, processing, transmission, and deletion. Each stage presents different risks and requires distinct protective measures. At rest, data must be encrypted and stored in secured environments. During processing, especially within cloud or shared resources, access must be strictly controlled and monitored. While in transit, data should travel through secured channels using modern encryption protocols. Even when data is no longer needed, proper deletion protocols must ensure complete removal, leaving no trace behind. This full-spectrum approach ensures that data remains secure regardless of its state or location.
Incorporating User-Centric Security Design
Security must also serve the user, not burden them. Overly complicated security measures can lead to errors, workarounds, or user frustration. Application interfaces must encourage secure behavior— clear prompts, simple verification steps, and visual indicators of trust to help users make safe decisions. Permission requests should be transparent and contextual, explaining why certain data or features are needed. Alerts and warnings should be informative, not alarming, guiding users through corrective action when needed. Educating users within the app ecosystem increases overall resilience, turning them into active participants in the security process.
Preparing for the Unknown
No system can promise absolute immunity from threats. What matters is readiness to respond when incidents occur. An effective incident response strategy ensures that when a breach or anomaly arises, the application can detect it, isolate it, and recover swiftly. Logging and monitoring tools help reconstruct the chain of events for investigation and resolution. Recovery plans should be tested regularly to ensure minimal downtime and data loss. Communication protocols must be clear— both internally for technical teams and externally for affected users or stakeholders. Proactive containment strategies make the difference between a minor issue and a public crisis.
How to Choose a Mobile App Development Company That Prioritizes Application Security?
Choosing a custom mobile app development company that prioritizes application security is a crucial step in building secure, reliable software. After understanding the importance of strong security practices and having a clear checklist in place, the next move is to find a development team that applies those standards consistently. Look for a company that practices secure coding, uses encryption for data, and follows authentication protocols aligned with industry expectations. They should conduct regular security testing, stay updated with platform-specific policies, and ensure apps are designed to detect threats like rooting or jailbreaking. A security-focused company will be transparent about the third-party tools they use and provide ongoing support to manage vulnerabilities post-launch. Effective communication and a commitment to continuous improvement are indicators of a development partner who understands that application security is an evolving responsibility. This alignment ensures that your application stays protected and trusted long after its release.
The Bottom Line
Application security is not defined by a single action but by an ongoing commitment to diligence, foresight, and adaptability. As applications continue to serve as gateways to vital data and services, securing them becomes an essential responsibility— not just for developers, but for organizations and users alike. From safeguarding mobile platforms to hardening web interfaces and preparing for unforeseen events, the practices outlined here form the foundation of a modern, sturdy security posture. Every step taken today helps build applications that users can trust tomorrow. Prioritizing security from the start also helps manage mobile app development cost more efficiently by preventing expensive fixes later. The goal is not just to create secure software, but to build digital ecosystems where safety is as seamless as functionality.
Partnering with a custom mobile application development company that values both innovation and security is essential for long-term success. Dreamer Technoland, a trusted software and mobile app development firm, prioritizes secure architecture, clean code, and thorough testing at every stage of the development process. Our approach ensures that applications are built to withstand real-world threats while delivering high performance and a seamless user experience. Whether you’re launching a new app or enhancing an existing one, our ability to align security with business goals makes us a dependable partner. With Dreamer Technoland, you gain more than just an app— you gain confidence in its security and sustainability. Reach out today to begin building mobile applications that are secure, future-ready, and tailored to your specific needs.